The referer header is an optional header that informs the website you are visiting of the URL of the previous website (assuming you clicked a link to get to the current site instead of typing the URL into the address bar). It has no good reason to exist, but those who want to track you around the internet really like it.
Most browsers in their default configuration populate the referer header. The following screenshots show https://browserleaks.com/ip loaded from other URLs.
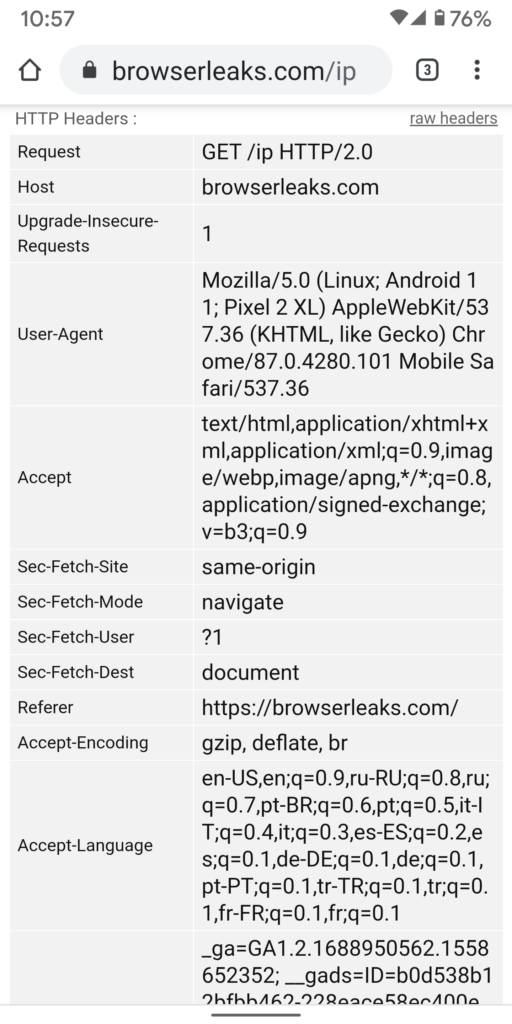

Privacy Browser, on the other hand, does not send the referer header on the base load of any URL.
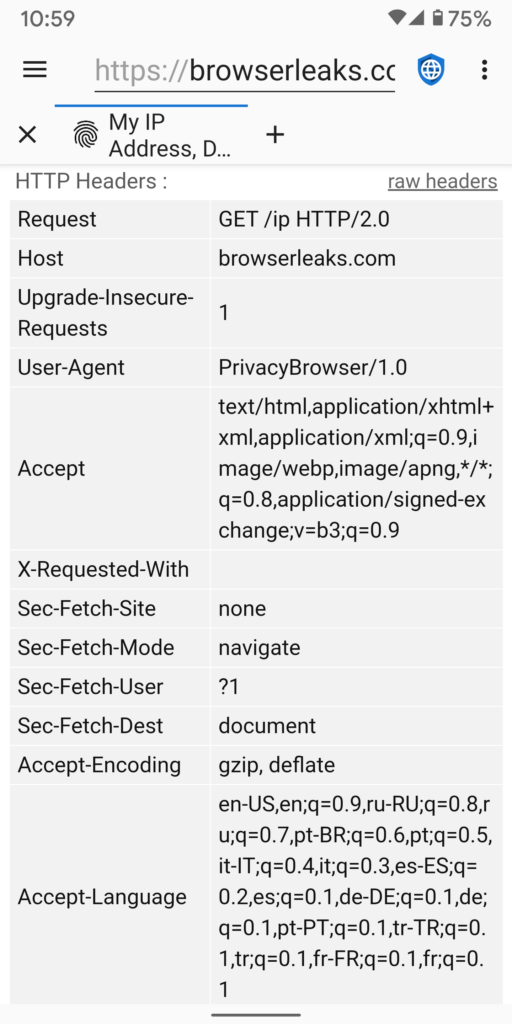
Some people have developed the habit of copying links into new tabs to prevent the sending of the referer header. This is an effective method on many browsers, but it isn’t needed on Privacy Browser.
When a base URL is loaded, it often loads a number of resources. Privacy Browser does currently send the referer header for these resource requests because Android’s system WebView doesn’t provide an easy way to override this behavior. But also because not doing so would break a number of websites that refuse connection to these resources if the referer header is not sent indicating the browser is viewing a URL on their domain.
For example, when Privacy Browser loads https://www.stoutner.com, irrespective of if it was loaded from a link at a different URL, no referer header is sent. The main HTML file at stoutner.com contains instructions to load a number of resources, as can be seen in the page source.
The requests activity shows this request being allowed by the blocklists.
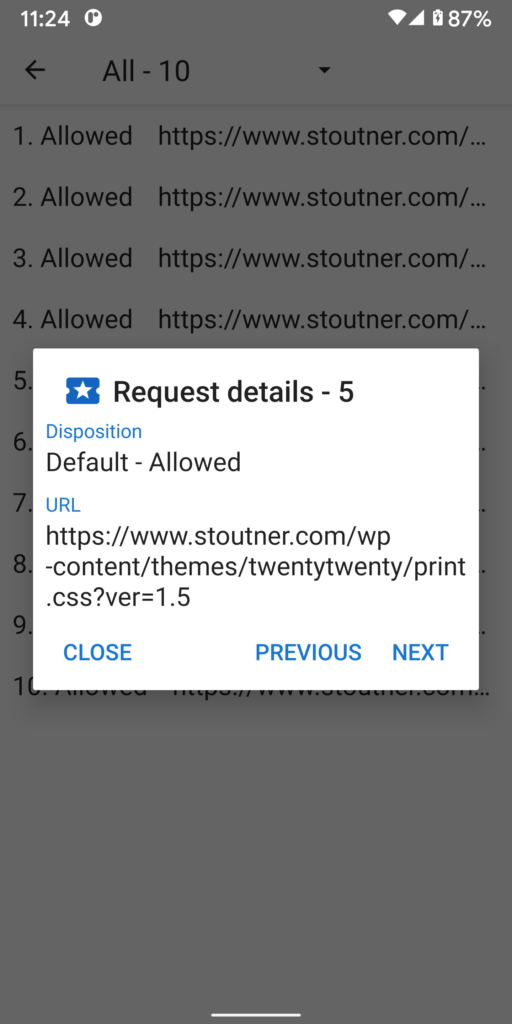
If I look at a forensic log on my Apache server, I can see the details of the request.
GET /wp-content/themes/twentytwenty/print.css?ver=1.5 HTTP/1.1|Host:www.stoutner.com|Connection:keep-alive|User-Agent:PrivacyBrowser/1.0|Accept:text/css,*/*;q=0.1|X-Requested-With:com.stoutner.privacybrowser.standard|Sec-Fetch-Site:same-origin|Sec-Fetch-Mode:no-cors|Sec-Fetch-Dest:style|Referer:https%3a//www.stoutner.com/|Accept-Encoding:gzip, deflate|Accept-Language:en-US,en;q=0.9,ru-RU;q=0.8,ru;q=0.7,pt-BR;q=0.6,pt;q=0.5,it-IT;q=0.4,it;q=0.3,es-ES;q=0.2,es;q=0.1,de-DE;q=0.1,de;q=0.1,pt-PT;q=0.1,tr-TR;q=0.1,tr;q=0.1,fr-FR;q=0.1,fr;q=0.1Here, the referer is shown as https%3a//www.stoutner.com/. There is a planned feature to disable the sending of the referer header by default on resource requests, along with a domain setting to specify the referer header. That should be part of the 3.x series, but at this point I think it likely it will not be implemented until after the desktop version of Privacy Browser.
Also, it should be noted that some websites prevent the downloading of files if the referer header is not set. For example, SpeedFan 4.52 cannot be downloaded on Privacy Browser because the web server denies all requests that do not have a referer header from www.almico.com. This will be fixed with the addition of the referer domain setting.
