Privacy Browser Android uses Android’s WebView to render web pages. WebView provides fairly limited controls compared to the upstream Chromium source. However, there are small set of user-configurable controls that Google has baked into WebView. Users can tweak these controls using WebView DevTools. If you are using a pre-stable channel (Beta, Dev, or Canary) there is a launcher icon for WebView DevTools. Users on the stable release of WebView are not provided with such a launcher, but it is possible for another program, like Privacy Browser, to include an intent that does launch it. Beginning with the 3.12 release, Privacy Browser has a WebView DevTools launcher in the navigation drawer.
By default, if you change any of the WebView flags, a persistent notification will be displayed in the status bar to warn you of how dangerous your life is. But that can be disabled if desired.
It is important to note that any changes made to WebView DevTools affects the way WebView works in all the apps on your device. These are not Privacy Browser specific settings. As such, it will affect any other browser based on WebView, like Lightning and FOSS Browser, as well as any other app that uses WebView to display documentation and information or interact with the internet (there are a number of apps that use WebView to handle logins). Privacy Browser will need to be restarted for any changes made in WebView DevTools to take effect. In addition, changes to WebView DevTools will need to be made on each of your devices and will not be carried over with an import of Privacy Browser’s settings to a new device.
The purpose of this page is to document any options in WebView that are likely to be of interest to Privacy Browser’s users. The available options can change with each WebView release. Note that some of the options come with warnings that they are experimental, and, particularly for those that involve site isolation or partitioning, might result in buggy behavior. If you become aware of any option that ought to be added to this page, feel free to post a suggestion to the forum.
X-Requested-With Header
The first flag that most users want to alter is WebViewXRequestedWithHeaderControl.
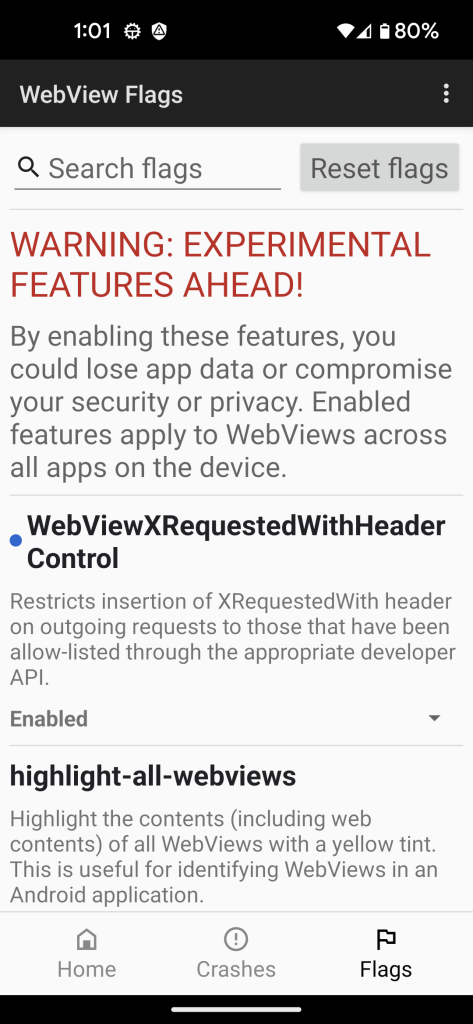
The X-Requested-With header is discussed in some depth in a separate post. Needless to say, Google is highly incentivized to make it easy to track you around the web, and adding this to Android’s WebView makes it easier to do so. I have found that companies like Google, who have such conflicts of interest, often have a very hard time setting defaults that are in the best interest of their users.
Site Isolation
The site-per-process flag enables site isolation.
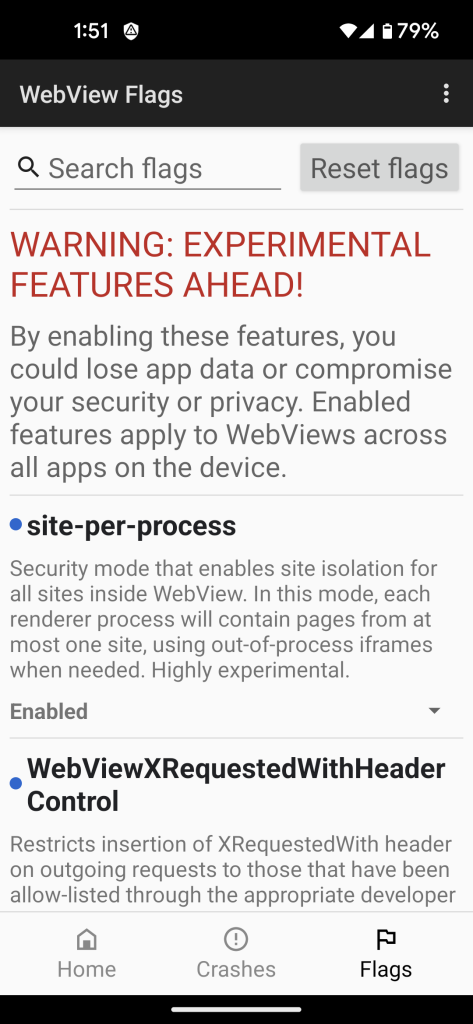
Site isolation adds an extra layer of protection against malicious JavaScript from one tab being able to steal data from another tab. It requires extra RAM to run each site in a separate tab, but in my testing it isn’t much of a noticeable difference.
Partitioned Cookies
PartitionedCookies is designed to protect against third-party cookie nonsense.
Don’t answer that. It is a rhetorical question. I already know the answer.
This shouldn’t ever be a problem with Privacy Browser because all third-party cookies are disabled. But it never hurts to have multiple layers of defense.
Third Party Storage Partitioning
Enabling ThirdPartyStoragePartitioning also requires enabling SupportPartionedBlogUrl, which are, combined, described as storage partitioning.
By default, Privacy Browser wipes all local storage every time Clear and Exit is run. But, if JavaScript is enabled on two tabs from different domains with a shared iframe that previously shared local storage, this will prevent one tab from tracking the other.
