I receive questions about WebRTC (Web Real-Time Communication) frequently enough that I thought it would be worthwhile to write a post about it.
First, a little bit of background about WebRTC for those who might not be familiar with it. It is a web standard for enabling video and audio chat in the browser. WebRTC connections are typically brokered by a server, but to enable efficient communication of audio and video, the clients exchange their IP information so they can communicate directly. Depending on the configuration of the software involved, if a user is trying to mask their IP address, WebRTC can be used by a server to discover their true IP addresses (both private and public IPv4 addresses as well as the IPv6 address).
WebRTC requires JavaScript to function. By default, JavaScript is disabled in Privacy Browser. So, those who use Privacy Browser with the default settings do not need to be worried about WebRTC leaking their IP addresses.
Some users have Tor Orbot proxy enabled or are otherwise using a VPN to mask their IP address but also need to have JavaScript enabled for some websites. By default, Orbot runs in proxy mode. The proxy controls in Android’s WebView allow proxying of general HTTP and HTTPS data but not WebRTC. In this configuration Privacy Browser will leak IP addresses through WebRTC when connected to Orbot. However, Orbot can also run in VPN mode, which will force all traffic from the device over Orbot.
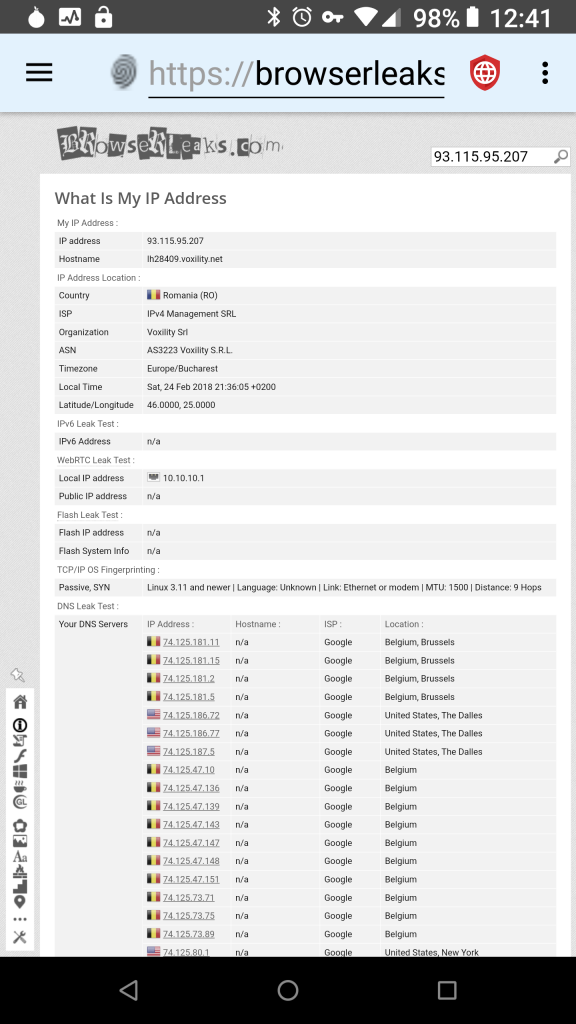
When Orbot is in VPN mode, Privacy Browser does not leak any IP address information via WebRTC as demonstrated by this screenshot from Browser Leaks. The key in the status bar at the top of the screen indicates that VPN mode is enabled. The local IP address listed is not the local IP address of the device, but rather the local IP address assigned by Tor, which in this case is 10.10.10.1.
Other VPN services will also mask the WebRTC IP address if they are configured correctly. Of course, the downside to using a VPN service is that then they can spy on everything you do and sell the information to the highest bidders.
There are some browsers that have support for disabling WebRTC completely, so that it can’t leak IP address information under any circumstances. Orfox and Fire.onion are two examples. Both of these browsers are modified versions of Firefox, and, as such, are able to disable WebRTC in the Gecko rendering engine. Privacy Browser currently uses Android’s built-in WebView as the rendering engine. Google does not provide a mechanism to disable WebRTC in WebView. However, in the 4.x series, I intend to create a rolling fork of WebView called Privacy WebView that will allow WebRTC to be completely disabled even when JavaScript is enabled.
To round out this conversation, I think it is important to point out that masking one’s IP address does not provide as much privacy as many people assume. The large technology companies have spent a lot of money building massive profiles of users, even those who are not their customers. These profiles contain much more detailed location information than an IP address discloses. And these systems are specifically designed to track users across IP addresses, because they want to track people from their homes, to their work, and across cell phone networks. Many of the technologies that companies use to track users are dependent on client devices running JavaScript. Blocklists like EasyPrivacy, which are included in Privacy Browser, are able to block some of this tracking, but they are not perfect. For users that need real privacy, the best defense is to browse the internet with JavaScript disabled.