Privacy Browser 2.5 has been released. It adds support for SSL certificate pinning in the domain settings. There is also a new Guide tab to explain the feature, which contains the following text:
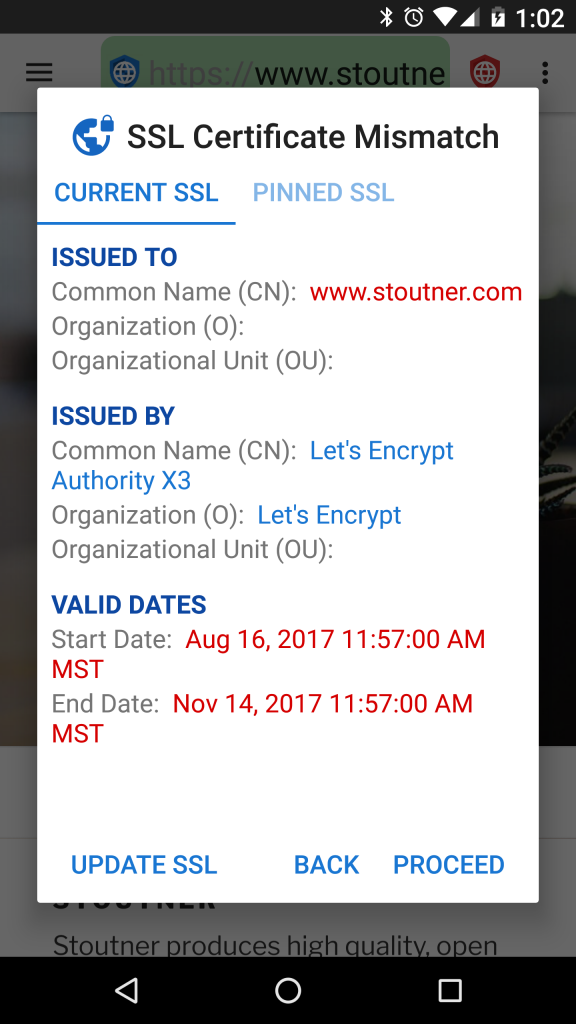
When visiting an encrypted URL (one that begins with HTTPS), the webserver uses an SSL certificate to both encrypt the information sent to the browser and to identify the server. The purpose of the server identification is to prevent a machine located between the browser and the webserver from pretending to be the server and decrypting the information in transit. This type of attack is known as a Man In The Middle (MITM) attack. SSL certificates are generated by certificate authorities: companies that verify a server’s identity and produce a certificate for a fee. Android has a list of trusted certificate authorities, and will accept any of their certificates for any website. It isn’t supposed to be possible for an organization to acquire an SSL certificate for a domain they do not control, but in practice many governments and large corporations have been able to do so.
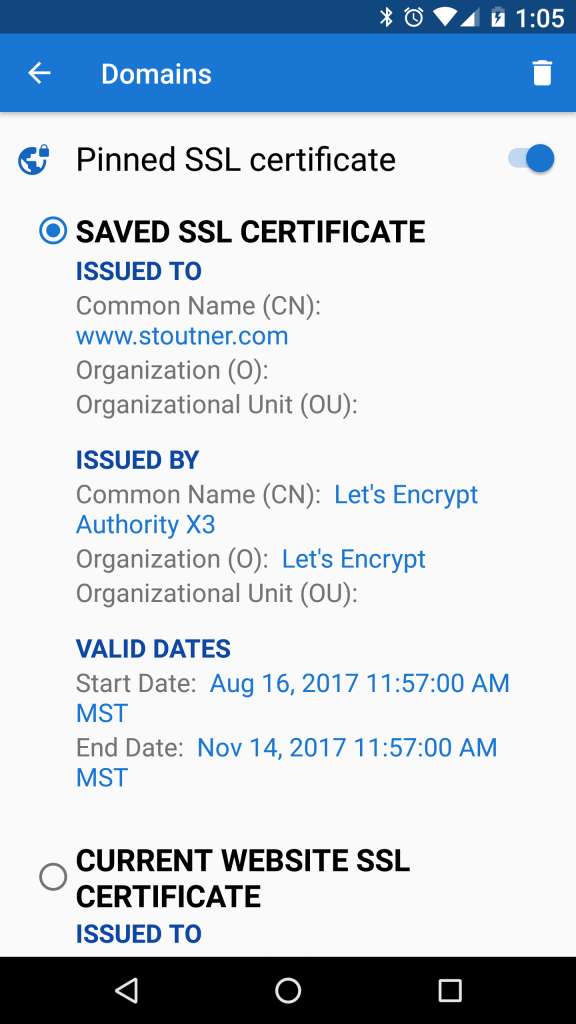
The purpose of SSL certificate pinning is to tell the browser that only one specific SSL certificate is to be trusted for a particular domain. Any other certificate, even if it is valid, will be rejected.
SSL certificates expire on a specified date, so even pinned SSL certificates will legitimately need to be updated from time to time. As a general rule, pinning SSL certificates probably isn’t needed in the majority of cases. But for those who suspect that powerful organizations may be targeting them, SSL certificate pinning can detect and thwart a MITM attack.
SSL certificates can be pinned in Domain Settings. Besides protecting against MITM attacks, pinning a self-signed certificate for a device like a wireless router or access point will remove the error message that is normally presented every time its website is loaded.
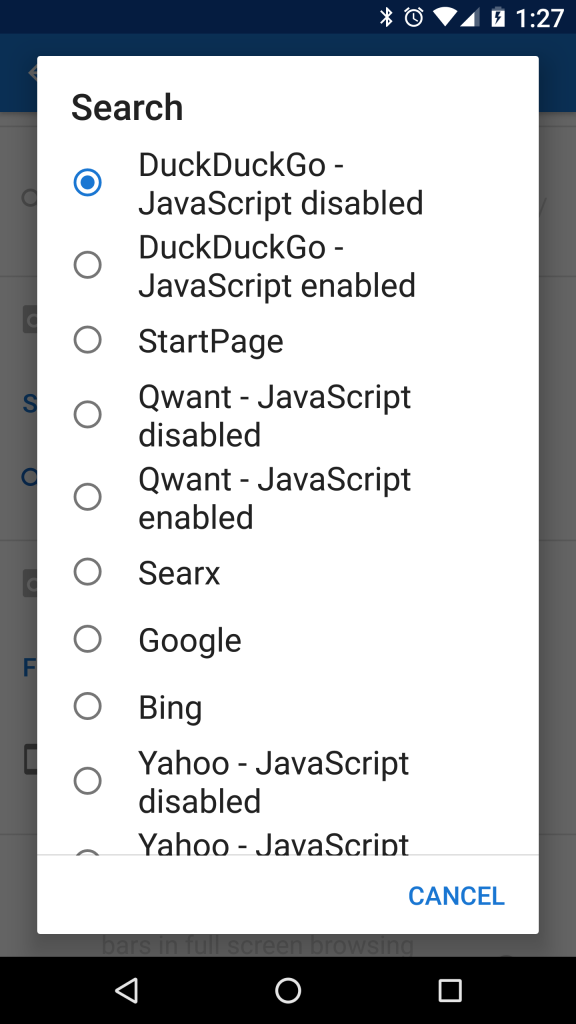
Searx.me was added to the list of default search engines, and the list was reorganized so that the privacy conscious search engines are listed before the others.
The default homepage has been updated to https://duckduckgo.com/?kao=-1&kak=-1, which works with both JavaScript enabled or disabled. This change will only affect new installations of Privacy Browser. Current users can chose to update their homepage if desired. The Onion site, https://3g2upl4pq6kufc4m.onion, is still broken when using the center search box unless JavaScript is enabled. Those who use this functionality might consider adding their voices to the Reddit thread on this topic.
A bug was fixed that caused the website title to be lost on rotate (and in some other circumstances). The website title is used when sharing a URL.
The options menu now indicates (via ghosting) if there is any DOM storage data that can be cleared. Previously, the entry was always enabled because WebView does not provide an easy way to tell if DOM storage data exists.
In the previous release, unencrypted websites were highlighted with a bold, red “http://” at the beginning of the URL. At the request of a user, the bold was removed and it is now just red text.
A bug was fixed that caused a URL to fail to load if a custom domain user agent was applied and the website performed a redirect on load. Another bug was fixed that caused changes a the website (like the sorting of a list) to be lost if Privacy Browser was moved to the background or otherwise restarted. Many small improvements were made to the Domains activity that should provide a smoother user experience.
Francesco Buratti provided an updated Italian translation and Jose A. León provided an updated Spanish translation.
The next release of Privacy Browser will enable HTTP authentication requests and implement a night mode.


One response to “Privacy Browser 2.5”
[…] problems with https://start.duckduckgo.com have been resolved by switching the default homepage to https://duckduckgo.com/?kao=-1&kak=-1. The problems with https://3g2upl4pq6kufc4m.onion remain and DuckDuckGo seems uninterested in […]